Wow! It has been a while I dropped anything here.
Well, I have been at Capturing some Flags lately and today I will be detailing a flag I helped capture.
A friend requested for help regarding Capturing a Flag for a task I suppose he got engaged in. I later found out that the task was a Forensics challenge for the angstromctf that came up in April, 2016.
The file provided for the challenge was duly downloaded and work began earnestly on it, to get the flag out.
A look at the file will indicate that it is a PDF, because of the .pdf extension. Oops! Having opened the file, the below error message appears.
With my little experience on CTFs, hints can always be derived from the subject of the challenge. On siting the task subject (headsup.pdf), I knew there was a pointer to the file header.
Using my favourite Hex Editor, I went ahead to view the file. Looking at the file header, I knew for certain that there was something wrong with the given file. Viewing the file headers, I came up with this:
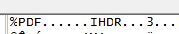
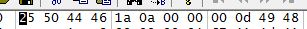
The %PDF is a standard header for every PDF. The wrong thing about this is the IHDR, which a typical header format for PNG files. To satisfy my curiosity, I decided to view how the file ends, using the hex editor, and I found this:

A typical PDF ends thus:

I now concluded that this could be a picture file and not a PDF. To be sure I was dealing with a picture file, I opened a picture file, with the .png extension with a hex editor and arrived at this:


The above gives a clear picture of how the file signature of a picture file (.png) looks like. Knowing this, I began to manually tweak the file headers to ensure it turns up a perfect PNG file. The tweaking entails my using the ‘Fill Selection’ tool, in the Edit menu to fix in the right hex strings using the hex editor.
After doing that, knowing well that the file was downloaded with a .pdf extension, I now change the extension to a .png.
Opening the file, I see this:

Flag captured!!!

